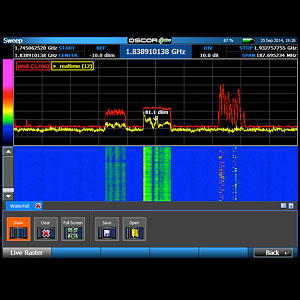
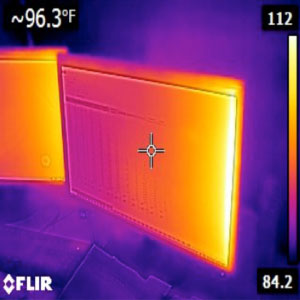
The Equipment
24 GHz range spectrum Analyser.
This item hunts and locates all Radio Frequency signals in the target area.
Telephone and Line Analyser
This item hunts and locates all Radio Frequency signals in the target area.
Non Linear Junction Detector
This NLJD hunts for hidden electronics not transmitting, or that have run out of power
Infra-red Camera
Forward Looking Infra-Red hunts for heat sources from hidden electronics
Borescope
This is used for inspecting smaller areas like air vents, drains, roofs
Acoustic Amplifier
This is used to amplify any microphones that have been set up in a target area
Inspection tools
These are required to check voltages, pull equipment and fixtures apart for inspection
Questions to ask all TSCM providers
- Do they have REI, shearwater, Audiotel or Winkelmann equipment?
- Have they been trained with manufacturer in the UK or USA?
- Can they prove it they have any training on paper?
Be careful of “Fly-by-nighters” and “Walter Mittys” who claim to have secret government/ armed forces/ police training; especially from overseas. Ask for proof of their job role and skill sets, or forget them. Just because someone was in the Police Force or Armed Forces doesn’t mean they have any specific TSCM training whatsoever.
Does the TSCM provider have at LEAST:
- A Spectrum Analyser
- A Non Linear Junction detector
- A telephone and line Analyser
- An Infra- Red Camera
- An RF Sniffer
- Wi-Fi Network analysis hardware and software
- VoIP inspection software
- Physical search inspection tool set
There is not one piece of equipment that can scan everything that has been invented in the world to date. Someone walking around with just a single small box and an antenna is a fraud.
This is just an absolute baseline to conduct a TSCM search, if a person doesn’t have all of these, he is a pretender hoping you don’t know what to look for, and is physically unable to do the job.
TSCM Experience and Training
- A TSCM operator must be able to prove where and when they were trained
- Security guards have NO knowledge or training in TSCM in Australia
- Licenced security risk assessors have no specific TSCM sweep training
What must be undertaken in a comprehensive TSCM sweep?
All Radio frequencies from bug transmissions and accounting for all signals in the area
All phones, phone lines, and IDF, MDF boards
A Physical search in conjunction with:
- A non-linear junction detector
- Infra-red camera
- Borescope
There is no point checking just for transmissions, if you are being recorded by a USB stick or a Dictaphone that doesn’t transmit.
There is no point in checking for transmitting and non-transmitting bugs only; if your phones are bugged, and picking up in room audio as well.
ANTI EAVESDROPPING RECOMMENDATIONS
Quickly lock down your operation:
- Check backgrounds of all service staff and subcontractors such as cleaners who work unsupervised.
- Have all staff to sign water tight confidentiality contracts written by an IP specialist lawyer, and a industrial relations lawyer. Include warnings that they will be prosecuted as a matter of company policy if they are caught stealing data.
- Designate a responsible person to ensure that all computer terminals are turned on and off at Master Mains power at the end of the working day. So they cannot be turned on by cleaners etc.
- Buy tougher locks to pick such as KABA MAS.
- Think of who would be your weakest link that a spy would target e.g. loosest on the phone, messy desk, thinks the regulations do not apply to him/her.
- Install an Intruder alarm system with motion detection SMS / email notifications of entry out of hours in high value areas to management.
- Put all staff through data safety training, and encourage them to keep an eye out for warning signs, and other staff privacy regulation breakages.
- Have a risk assessment conducted by a qualified security risk assessor to find any and all gaps in your business’s security, and implement the recommendations to close the gaps.
- Create a security informed and aware culture in the business.
- Immediately respond to negative workers.
Most importantly: get your place swept by a competent TSCM technician to find out if you are being electronically attacked
New IT security Company policy:
- No USB sticks in the office except those provided by management with Identifiers.
- All company paper must be shredded onsite by the end of the day.
- All confidential information must be stored in a designated locked storage area.
- Passwords must be changed every 4 weeks.
- Computers must be set to sleep after 15minutes of inactivity.
- Computers must be logged off at all breaks and when away from the computer.
- No access to personal email, social media or personal phones inside work times or premises.
- Staff will be instantly dismissed for using another staff member’s computer, laptop, mobile device, desk phone or mobile phone without permission from their manager.
- All employees who are leaving will be closed off from accessing or removing company data once they have left.
- Enforce all staff to have a Clear desk at the end of their shift, and lock up all sensitive information.
Jobs for your IT Security Specialist
- Encrypt all sensitive electronic data immediately.
- Secure all your computer network, data and communications.
- Install an industrial grade firewall and virus scanner.
- Get your computer network to be able to log, monitor and audit employee online activity.
- Lock off sensitive data access with limited access to only those who have need of it, by department e.g. accounting/ marketing/ production/ sales.
- Have a secure data backup and recovery process.